
About ISMS 

There remains an overwhelming tendency for organizations to focus on the tactical and technical aspects of Information Technology Security. This results in creating an information security program comprised of an ad hoc collection and aggregation of technical controls and countermeasures with little regard for the context of organizational business environment, strategies, goals & objectives, business processes, compliance requirements and risks.
An Information Security Management System (ISMS) facilitates a migration beyond the traditional perspective of IT Security toward the development of enterprise Information Security programs that provide efficient and effective information asset protection in the context of each individual organization’s requirements.
An ISMS is an “overall management system, based on a business risk approach, to establish, implement, operate, monitor, review, maintain and improve information security The management system includes organizational structure, policies, planning activities, responsibilities, practices, procedures, processes and resources.” Section 3.7 of ISO 27001
The role of an ISMS is to protect the confidentiality, integrity, and availability of an organization’s information assets and infrastructure.
An ISMS focuses on the security of information at the strategic, tactical, and operational levels, concerned with information in any form - written, oral, or electronic, in any state - transit, stored, or processed, encompassing people, processes, and technology. This unified approach to information asset protection is based on eleven major elements that address security strategy and architecture.
The eleven major elements of an ISMS are:
Security Policy
Organization of Information Security
Asset Management
Human Resources Security
Physical and Environmental Security
Communications and Operations Management
Access Control
Information Systems Acquisition, Development and Maintenance
Information Security Incident Management
Business Continuity Management
Compliance
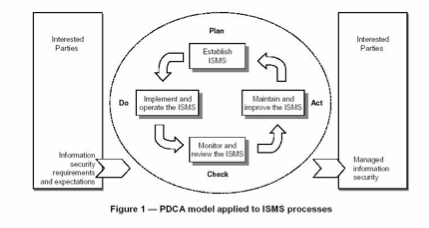
Recognizing that information security is an ongoing process and not a product, the ISMS framework uses a Plan - Do - Check - Act process to ensure that the ISMS remains relevant to the organization as a sustainable management system and not a one time project.
I